In today’s digital age, the term “blacklist” has become increasingly relevant, especially within the realm of cybersecurity. A blacklist is essentially a list of entities—such as individuals, organizations, or IP addresses—that are deemed undesirable or potentially harmful. This concept, though simple in theory, plays a crucial role in protecting systems, networks, and users from malicious activities.
Understanding what a blacklist is and how it functions can help individuals and organizations better safeguard their digital assets. In this article, we’ll explore the definition of a blacklist, its various applications, and why it’s vital in the context of cybersecurity.
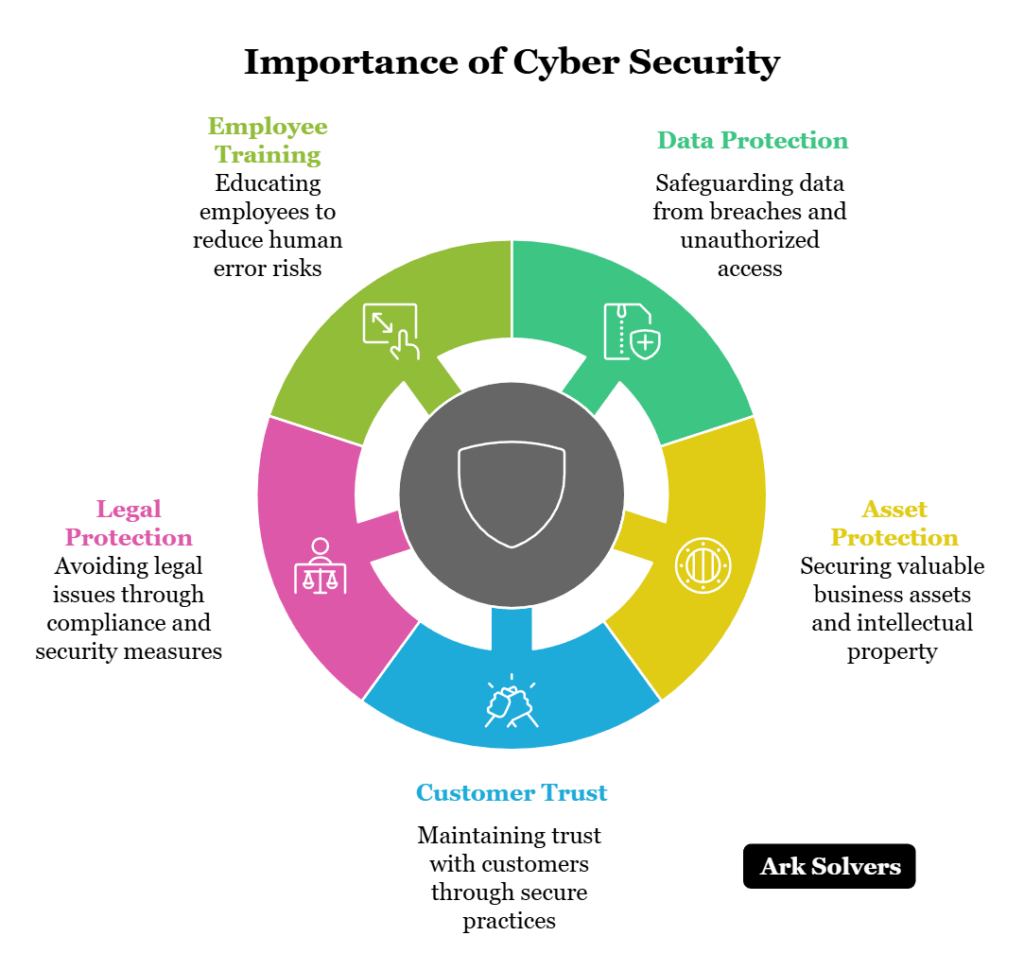
What Is a Blacklist?
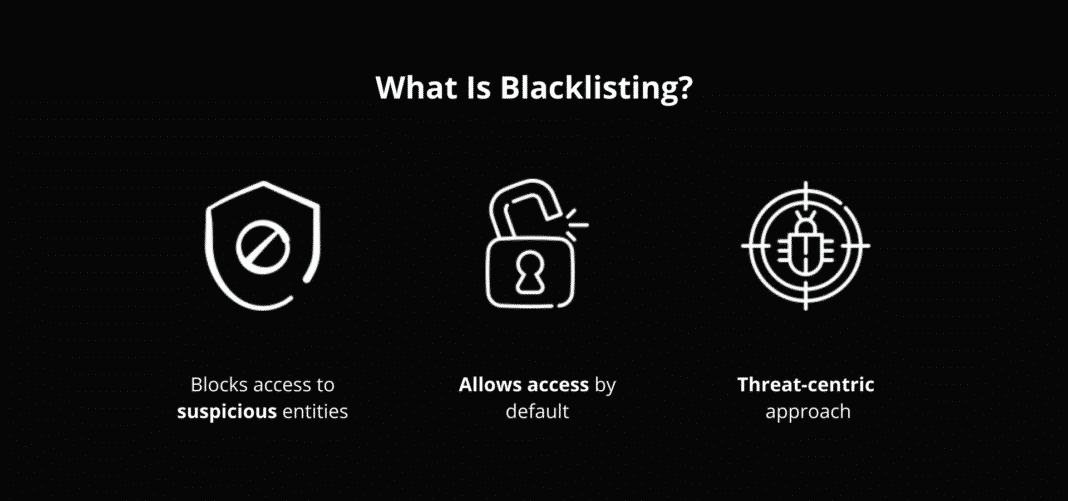
A blacklist is a list of items that have been identified as problematic or dangerous. These lists can be used to exclude certain entities from accessing systems, services, or resources. In the context of cybersecurity, blacklists are commonly used to block access to known malicious IP addresses, domains, or email servers that are associated with spam, phishing, or other cyber threats.
Blacklists have been around for centuries, but they have taken on new significance in the digital world. From historical examples like the Hollywood blacklist during the 1940s and 1950s, where individuals were excluded from employment due to political beliefs, to modern-day cybersecurity measures, the concept of a blacklist continues to evolve.
Types of Blacklists
There are several types of blacklists, each serving a specific purpose:
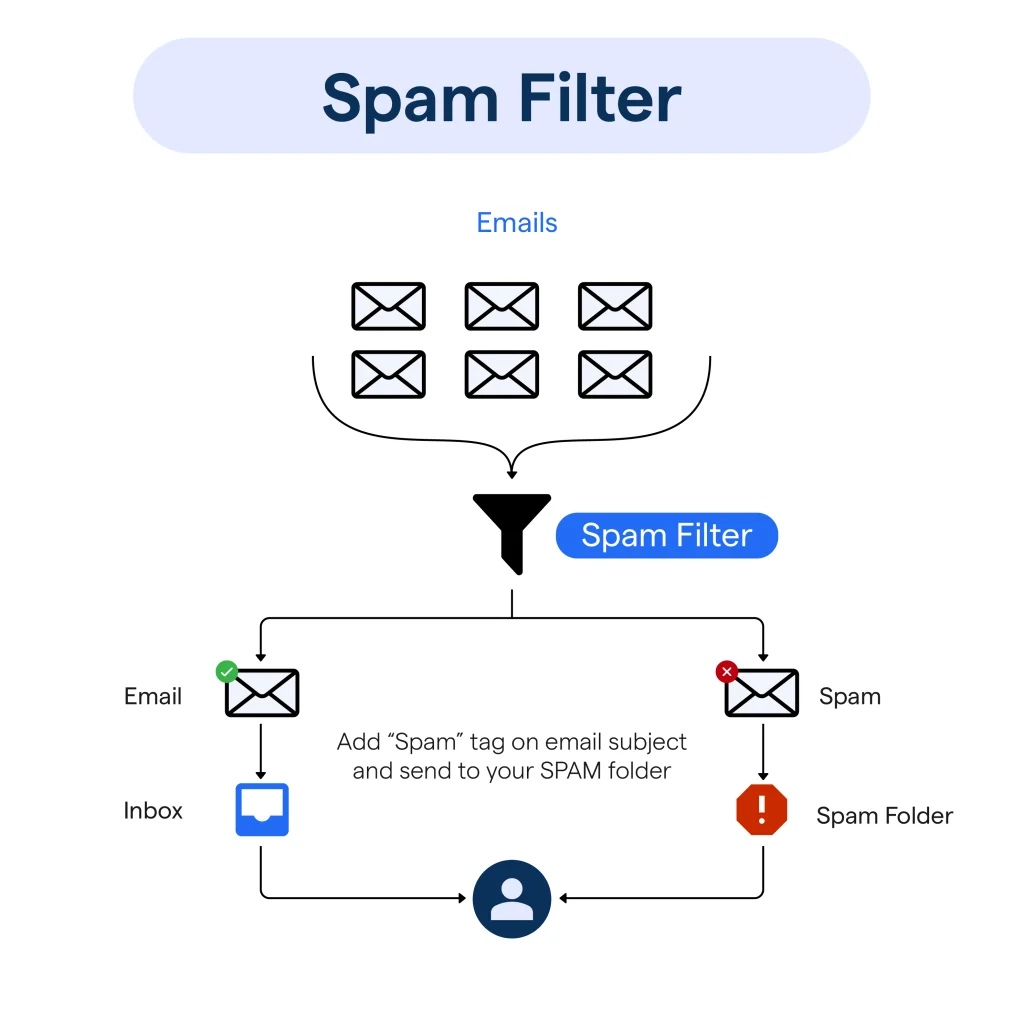
1. Real-Time Blacklists (RBLs)
Real-Time Blacklists (RBLs) are a critical tool in the fight against spam and other malicious online activities. These lists identify IP addresses or domains that are known to send unsolicited emails or engage in phishing schemes. RBLs are often distributed via DNS and are used by email servers to filter out potentially harmful messages.
There are two main methodologies for compiling RBL data:
-
Crowd Sourced: This involves users flagging suspicious emails as spam. When enough users mark an email as spam, the sender’s IP address is added to the RBL.
-
Honey Pots: These are decoy email addresses that are never used for legitimate purposes. Any email sent to these addresses is considered spam and is added to the RBL.
2. URI Blackhole Lists (URIBLs)
URIBLs are another type of blacklist that focuses on domain names associated with spam or phishing activities. Unlike traditional RBLs, which focus on IP addresses, URIBLs target websites that are known to distribute malicious content.
These lists are particularly useful for web administrators who want to protect their users from visiting harmful websites.
3. Credit Blacklists
In addition to cybersecurity, blacklists are also used in financial contexts. Credit reports, for example, function as blacklists by identifying individuals who are considered high-risk borrowers. These reports can affect a person’s ability to obtain credit, loans, or even employment.
The Role of Blacklists in Cybersecurity
Blacklists play a vital role in enhancing cybersecurity by helping to identify and block potential threats. Here are some key reasons why they are important:
1. Preventing Spam and Phishing Attacks
By using RBLs, organizations can significantly reduce the amount of spam and phishing emails that reach their users. Email servers can automatically block messages from IP addresses or domains listed on an RBL, thereby protecting users from malicious content.
2. Protecting Against Malware and Viruses
Blacklists are also used to block access to websites that are known to host malware or viruses. Web browsers and security software often use these lists to warn users about potentially dangerous sites.
3. Enhancing Network Security
Network administrators can use blacklists to restrict access to certain IP addresses or domains that are associated with cyber threats. This helps to prevent unauthorized access and reduces the risk of data breaches.
4. Compliance and Legal Requirements
Many industries are required by law to implement certain security measures, including the use of blacklists. For example, the Fair Credit Reporting Act (FCRA) in the United States requires that individuals have access to their credit reports, which can act as a form of blacklisting.
The Importance of Blacklists in Today’s Digital World
As the internet becomes more integrated into our daily lives, the need for robust security measures has never been greater. Blacklists provide a powerful tool for identifying and mitigating threats, making them an essential component of any cybersecurity strategy.
However, it’s important to note that not all blacklists are created equal. Some may be unreliable or even biased, which can lead to false positives or unfair exclusion of legitimate users. Therefore, it’s crucial to use reputable blacklists and to regularly review and update them to ensure accuracy and fairness.
Conclusion
In summary, a blacklist is a valuable tool in the fight against cyber threats. Whether it’s used to block spam emails, prevent access to malicious websites, or identify high-risk borrowers, blacklists serve a critical function in maintaining security and trust in the digital world.
As technology continues to evolve, so too will the methods used to combat cyber threats. Staying informed about the latest developments in blacklisting and cybersecurity is essential for both individuals and organizations looking to protect themselves in an increasingly connected world.
Author: John Doe
Title/Role: Cybersecurity Analyst
Credentials: John Doe is a certified cybersecurity analyst with over a decade of experience in protecting digital assets. He specializes in threat detection, network security, and data privacy.
Profile Link: LinkedIn Profile
Sources:
1. Cybersecurity & Infrastructure Security Agency (CISA)
2. Federal Trade Commission (FTC)
3. National Institute of Standards and Technology (NIST)
Internal Links:
1. Understanding Cyber Threats
2. Best Practices for Email Security
3. The Role of Firewalls in Network Protection
Call to Action: Stay updated with the latest news and insights on cybersecurity and digital safety. Explore our resources to learn more about how to protect yourself and your organization from emerging threats.
URL Slug: what-is-a-blacklist-cybersecurity
Image Optimization:
– 
–
– 
– 
–
Schema Markup:
{
"@context": "https://schema.org",
"@type": "Article",
"headline": "What Is a Blacklist? How It Works and Its Importance in Cybersecurity",
"datePublished": "2025-04-05",
"author": {
"@type": "Person",
"name": "John Doe"
},
"publisher": {
"@type": "Organization",
"name": "Tech Security Insights",
"logo": {
"@type": "ImageObject",
"url": "https://example.com/logo.png"
}
}
}










More Stories
What Is Yodo Para Tiroides and How Does It Affect Thyroid Health?
How to Claim Your Joy in League of Legends: A Step-by-Step Guide
What is WSET? A Comprehensive Guide to Wine Education